Protecting Sensitive Information with Temporary Storage
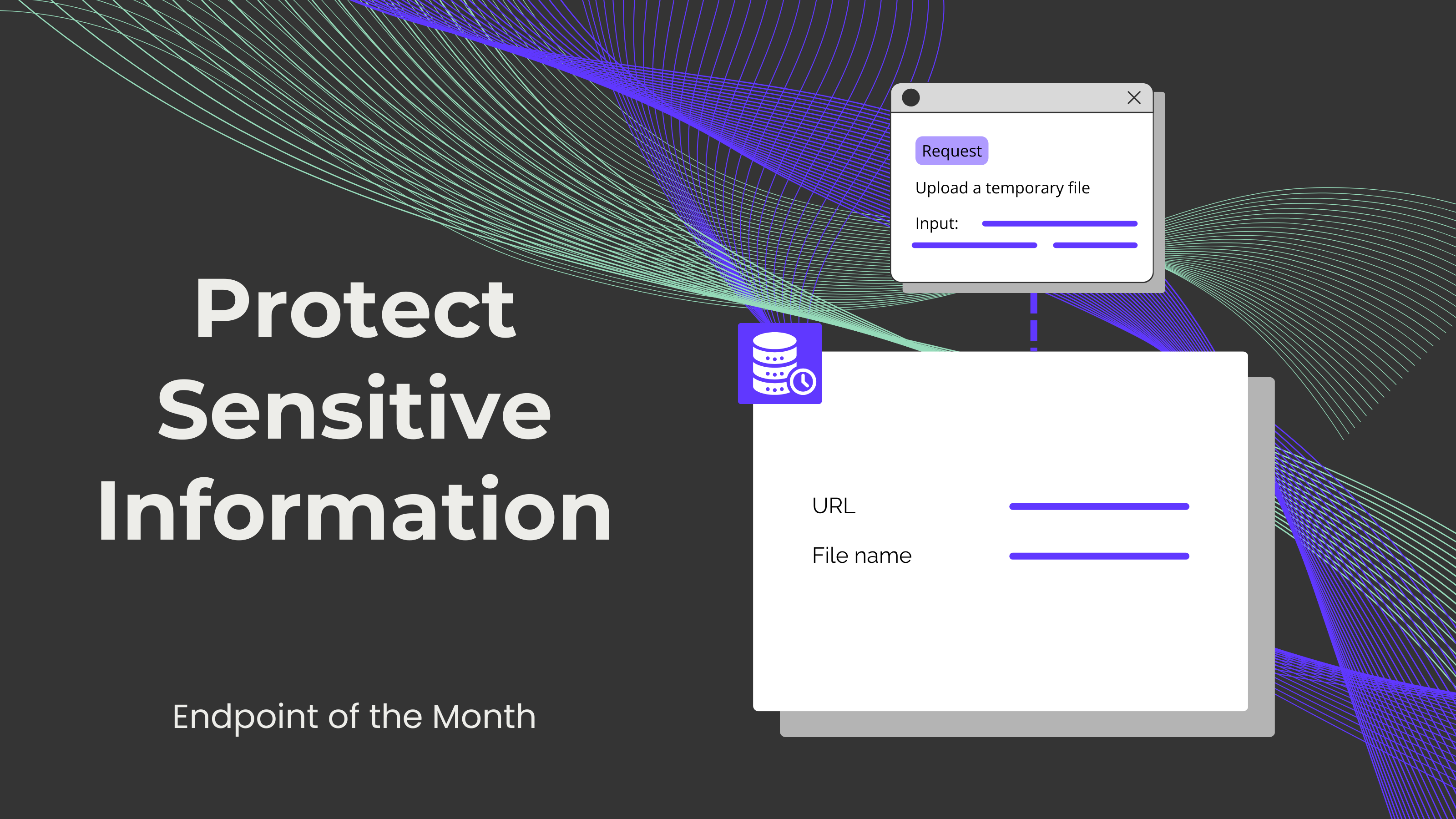

Data is everywhere - in everything you read, in everything you see, wherever you are. For this same reason, it is crucial to recognize the importance of data and its great potential to influence decisions, processes, operations, and more. Therefore, protecting all sorts of information has become one of the top priorities for many individuals, professionals, and businesses. However, handling that much sensitive information and complying with certain regulations can be overwhelming. That is why, in this blog, we would like to present a great solution for this kind of problem: temporary storage.
Some examples of temporary storage solutions are cloud-based services and secure file-sharing platforms, which can help minimize the expiry of sensitive information by storing it for a limited time. This not only eliminates all probabilities for any set of risks, but it also makes unauthorized access or data breaches impossible.

However, as amazing as temporary storage can sound, it can also raise a lot of concerns about data privacy. To begin with, companies must ensure, when using any temporary storage solution, that they are complying with data privacy standards, such as the General Data Protection Regulation (GDPR). This is essential, since not complying with these standards can lead to severe legal consequences and damage their reputation.
Additionally, data encryption can be another way to safeguard data privacy. Companies can develop encryption protocols that protect data when stored and when shared, ensuring that certain information cannot be accessed even when security measures have been breached. Moreover, they can implement access control to also monitor who has access and retrieve sensitive information.
Furthermore, companies should also implement data retention policies and establish some rules and guidelines for employees that dictate how, where, and how long data will be stored, how it will be accessed, and when it will be deleted. With such a framework, companies can ensure that confidential information will not be kept longer than needed and that they won't be exposed to a lot of risks.
Besides, employers and employees can also undergo training and user awareness programs to make them aware of the risks associated with data storage. This way, they can understand and learn best practices to handle situations when handling data, but most importantly, when avoiding sharing this information over insecure channels.
Last but not least, companies can implement auditing mechanisms to monitor the access and usage of such information. With regular audits, they can track the usage of data and identify abnormal patterns or any security concerns early on. This makes sure that problems can be addressed before they escalate, which strengthens the integrity and privacy of stored data.